O que é xmlrpc.php no WordPress e por que você deve desativá-lo
O WordPress sempre teve recursos embutidos que permitem que você interaja remotamente com o seu site. Às vezes, você precisa acessar seu site e seu computador não vai estar disponível para isso.
Por muito tempo, essa solução era o arquivo xmlrpc.php. Desde os primórdios do WordPress, foram incorporados recursos que permitiram que o WordPress se comunicasse com outros sistemas. Mas nos últimos anos, xmlrpc.php se tornou mais um problema do que uma solução.
Neste artigo nós vamos explicar o que é xmlrpc.php realmente é e porque ele foi criado. Também analisamos os problemas comuns de segurança que ele causa e como corrigi-los em seu próprio site WordPress.
Conteúdo
O que é xmlrpc.php?
O XML-RPC é um recurso do WordPress que permite que dados sejam transmitidos, com HTTP agindo como mecanismo de transporte e XML como mecanismo de codificação. Como o WordPress não é um sistema “fechado” e, ocasionalmente, precisa se comunicar com outros sistemas, esse sistema foi feito para lidar com esse trabalho.
Por exemplo, digamos que você queira postar no seu site a partir do seu dispositivo móvel, já que está sem um computador. Você poderia usar o recurso de acesso remoto ativado por xmlrpc.php para fazer exatamente isso.
Com o xmlrpc.php habilitado, você consegue se conectar ao seu site via smartphone, implementando trackbacks e pingbacks de outros sites, e algumas funções associadas ao plugin Jetpack.
Por qual motivo foi criado e como foi usado?
Você já sabe o que é xmlrpc.php, agora resta saber o motivo da criação. Bom, a implementação do XML-RPC vem desde os primórdios do WordPress, antes mesmo de se tornar WordPress. No início da internet, quando as conexões eram incrivelmente lentas, o processo de escrever e publicar na web era muito mais difícil e demorado. Ao invés de escrever no próprio navegador, a maioria das pessoas escrevia offline, depois copiava e colava o conteúdo na web. Ainda assim, esse processo estava longe de ser ideal.
A solução (na época) era criar um cliente de blog offline, onde você poderia compor seu conteúdo, depois conectar-se ao seu blog para publicá-lo. Essa conexão foi feita através do XML-RPC. Com a estrutura básica do XML-RPC funcionando, os primeiros aplicativos usavam essa mesma conexão para permitir que as pessoas acessassem seus sites do WordPress de outros dispositivos.
XML-RPC hoje
Em 2008, com a versão 2.6 do WordPress, havia uma opção para ativar ou desativar o XML-RPC. No entanto, com o lançamento do aplicativo WordPress para iPhone, o suporte a XML-RPC foi habilitado por padrão e não havia opção para desativar a configuração. Isso permanece até hoje.
No entanto, a funcionalidade desse arquivo diminuiu bastante com o tempo, e o tamanho geral do arquivo diminuiu de 83 kb para 3 kb, de modo que ele não desempenha um papel tão grande quanto costumava.
XML-RPC no futuro
Com a nova API do WordPress, podemos esperar que o XML-RPC seja totalmente eliminado. Hoje, essa nova API ainda está em fase de teste e só pode ser ativada com o uso de um plugin. No entanto, você pode esperar que, no futuro, a API seja codificada diretamente no núcleo do WordPress, o que eliminará a necessidade do arquivo xmlrpc.php. A nova API não é perfeita, mas fornece uma solução mais robusta e segura para o problema que o xmlrpc.php tenta solucionar.
Por que você deve desativar xmlrpc.php
Agora que você já sabe o que é xmlrpc.php e como funciona, precisa entender o principal, que são os problemas que ele traz. Os maiores problemas com o XML-RPC são as preocupações de segurança que surgem. Os problemas não estão diretamente com o XML-RPC, mas sim como o arquivo pode ser usado para ativar um ataque no seu site.
Claro, você pode se proteger com senhas fortes e plugins de segurança do WordPress. Mas o melhor modo de proteção é simplesmente desativá-lo. Existem duas principais fraquezas do XML-RPC que foram exploradas no passado.
O primeiro é usar ataques para entrar no seu site. Um invasor tentará acessar seu site usando xmlrpc.php e tentando várias combinações de nome de usuário e senha. Eles podem efetivamente usar um único comando para testar centenas de senhas diferentes. Isso permite que eles ignorem as ferramentas de segurança que normalmente detectam e bloqueiam esses tipos de ataque.
O segundo foi derrubar um site realizando um ataque DDoS. Hackers usariam o recurso pingback no WordPress para enviar pingbacks para milhares de sites instantaneamente. Esse recurso em xmlrpc.php fornece aos hackers um suprimento quase infinito de endereços IP para distribuir um ataque DDoS.
Para verificar se o XML-RPC está sendo executado em seu site, você pode checar através de uma ferramenta chamada XML-RPC Validator. Execute seu site por meio da ferramenta e, se você receber uma mensagem de erro, isso significa que você não tem o XML-RPC ativado.
Se você receber uma mensagem de “sucesso”, indicando que o XML-RPC está sendo executado dentro do seu site, você poderá interromper o xmlrpc.php com uma das duas abordagens abaixo.
Método 1: Desativando xmlrpc.php com plugins
Essa maneira de desativar o xmlrpc.php é muito simples e fácil. Basta entrar no painel de controle do seu site WordPress e ir até a seção Plugins › Adicionar novo. Procure pelo plugin Disable XML-RPC e instale-o.
Ative o plug-in e está tudo pronto. Este plugin vai inserir automaticamente o código necessário para desativar o XML-RPC. No entanto, lembre-se de que alguns plugins existentes podem utilizar partes do XML-RPC, portanto, desabilitá-lo completamente pode fazer com que um conflito de plug-in ou certos elementos do site não funcionem mais.
Se você deseja desativar determinados elementos do XML-RPC, mas ainda permitir que certos plugins e recursos funcionem, use os seguintes plugins:
- Stop XML-RPC Attack: Esse plugin vai interromper todos os ataques de XML-RPC, mas continuará permitindo que plugins como o Jetpack e outras ferramentas e plugins automáticos mantenham o acesso ao arquivo xmlrpc.php.
- Control XML-RPC Publishing: Isso permite que você mantenha o controle sobre a opção de publicação remota oferecida pelo xmlrpc.php.
Método 2: Desativando xmlrpc.php manualmente
Se você não quiser usar um plugin e preferir fazê-lo manualmente, siga esta abordagem. Ele vai interromper todas as solicitações xmlrpc.php recebidas antes de serem passadas para o WordPress. Abra seu arquivo .htaccess. Você pode ter que ativar o “show hidden files” no gerenciador de arquivos ou no seu cliente FTP para localizar esse arquivo. Dentro do seu arquivo .htaccess, cole o seguinte código:
Conclusão
No geral, o XML-RPC foi uma solução sólida para alguns dos problemas que ocorreram devido à publicação remota em sites WordPress. No entanto, com esse recurso, surgiram algumas falhas de segurança que acabaram sendo muito prejudiciais para alguns proprietários de sites do WordPress.
Para garantir que seu site permaneça seguro, é uma boa ideia desabilitar o xmlrpc.php por completo. A menos que você precise de algumas das funções necessárias para publicação remota e o plugin do Jetpack. Caso precise, você deve usar os plugins de solução alternativa que permitem esses recursos, enquanto ainda corrige as falhas de segurança.
Com o tempo, podemos esperar que os recursos do XML-RPC se integrem na nova API do WordPress, que manterá o acesso remoto, sem sacrificar a segurança. Mas, enquanto isso, é uma boa ideia proteger-se dos potenciais buracos de segurança do XML-RPC.
Agora que você entendeu o que é xmlrpc.php, nós perguntamos: Você bloqueou o acesso ao XML-RPC por meio de um plugin ou manualmente? Teve algum problema de segurança dentro do seu site por causa da ativação do xmlrpc.php? Por favor, compartilhe sua experiência nos comentários abaixo.
O Autor
Ariane G. / @arianegoncalves
A Ari é gerente de SEO na Hostinger Brasil e está há mais de três anos na equipe. Ela já colaborou com produção e localização de tutoriais, localização de landing pages, e hoje atua com foco em SEO para garantir o posicionamento da Hostinger nos mecanismos de busca.
***************
55 Shares
pt
WordPress site hacked. If it happens to you, it’s tempting to panic. In this post, I’ll help you identify if your site has been hacked, take you through steps to clean your site and help you make it more secure.
Finally, I’ll give you some tips to prevent your WordPress site from being hacked again in the future.
Ready? Take a deep breath, and let’s get started.
WordPress Hacked: Signs Your WordPress Site Is at Risk
Your WordPress site isn’t behaving as it should do. But how do you know that problem is due to a hack? Let’s take a look at some of the signs that your site has been hacked:
- You can’t log in.
- Your site has changed without you having done anything (for example, the homepage has been replaced by a static page or new content has been added).
- Your site is redirecting to another site.
- When you or other users try to access your site, you get a warning in your browser.
- When you search for your site, Google gives a warning that it may have been hacked.
- You’ve received a notification from your security plugin of a breach or an unexpected change.
- Your hosting provider has warned you about unusual activity on your account.
Let’s take a look at each of these in more detail.
You Can’t Log In
If you can’t log in to your site, it may be a sign that your site has been hacked. However, it’s more likely that you’ve just forgotten your password. So before you assume you’ve been hacked, try resetting your password. If you can’t, that’s a warning sign. Even if you can, you may still have been hacked and you’ll have to do a bit more investigating.
Hackers sometimes remove users or change user passwords to prevent access. If you’re unable to reset your password, your user account could have been removed, which is a sign of hacking.
Your Site Has Changed
One form of hacking is to replace the homepage with a static page. If your site looks completely different and isn’t using your theme, it’s probably been hacked.
The changes may be more subtle, maybe adding spurious content, or links to unsavory sites. If your footer is full of links that you didn’t add, and especially if those links are hidden or in a tiny font size, you could have been hacked.
Before you assume you’ve been hacked, check with other site administrators or editors, to be sure they haven’t accidentally made the changes.
If your theme isn’t from a reputable source and you’ve recently updated it, that could be the culprit.
Your Site is Redirecting
Sometimes hackers will add a script that redirects people to another site when they visit yours. This will probably be a site you don’t want your users being taken to.
This happened to me when a school site I managed was redirecting to a dating site. As you can imagine, my client wasn’t pleased and had to drop everything else I was doing and fix it straight away. It turned out that it was an insecurity on the server, not on my site, which is one reason to only use quality hosting. I switched hosting provider as soon as possible and fixed the hack almost immediately.
Browser Warnings
If your browser is warning that your site is compromised, it could be a sign that your site has been hacked. It could also be due to some code in a theme or plugin that you need to remove, or an issue with domains or SSL.
Refer to the advice given with the warning in your browser to help you diagnose the problem.
Search Engine Warnings
When you search for your site, if it’s been hacked, Google may display a warning. This could mean that the sitemap has been hacked, which would affect the way Google crawls your site. Or it may be a bigger problem: you’ll need to do the diagnosis below to find out exactly what’s happened.
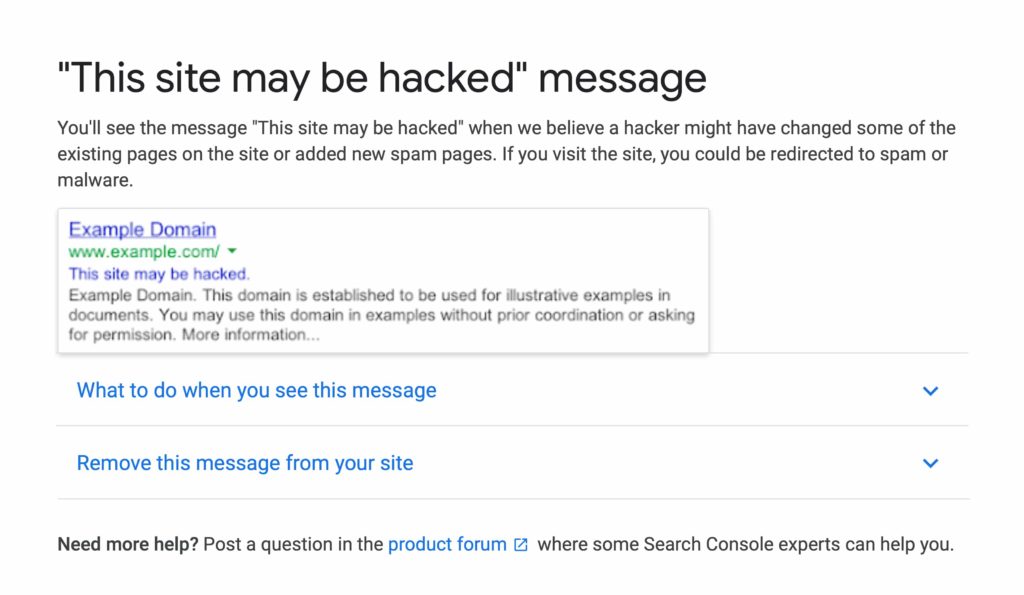
Google alert – this site may have been hacked
Why WordPress Sites Get Hacked
There are plenty of reasons why WordPress sites get hacked, but here’s an overview of the most common factors.
1. Insecure Passwords
This is one of the most frequent causes of hacking. The most commonly used password in the world is “password”. Secure passwords are necessary not just for your WordPress admin account, but for all your users and all aspects of your site including FTP and hosting.
2. Out of Date Software
Plugins and themes, as well as WordPress itself, are subject to security updates which need to be applied to your site. If you don’t keep your themes, plugins, and version of WordPress up to date, you’re making your site vulnerable.
3. Insecure Code
Plugins and themes that aren’t from reputable sources could be introducing vulnerabilities to your site. If you need free WordPress themes or plugins, install them from the official theme directory.
When buying premium themes and plugins, be sure to check the vendor’s reputation and get recommendations from people and sources you trust. Never install nulled plugins, which are premium plugins from free sites, designed to cause harm, or collect information.
How Does WordPress Get Hacked?
If you want to know more about how WordPress sites get hacked (and you aren’t rushing ahead to the steps to take if your own site has been hacked), here are the main routes hackers take to get into your site:
- Backdoors – these bypass normal methods of accessing your site, e.g. via scripts or hidden files. An example was the Tim Thumb vulnerability in 2013.
- Pharma hacks – an exploit used to insert rogue code into out of date versions of WordPress.
- Brute-force login attempts – when hackers use automation to exploit weak passwords and gain access to your site.
- Malicious redirects – when backdoors are used to add malicious redirects to your site.
- Cross-site scripting (XSS) – the most common vulnerability found in WordPress plugins, these inject scripts that then allow a hacker to send malicious code to the user’s browser.
- Denial of Service (DoS)- when errors or bugs in a website’s code are used to overwhelm a website so it no longer functions.
If you’re running an ecommerce site, make sure to read our in-depth guide on Ecommerce Fraud Prevention.
These all sound pretty scary but there are steps you can take to protect your WordPress site against them. First, let’s work through the steps you need to take when your site is hacked.
WordPress Site Hacked: What to Do (Step-By-Step Guide)
If your site is hosted with Kinsta, we have a hack-free guarantee, which means we will work through your site and remove the hack. If you’re with another hosting provider, you’ll need to involve them, but you may need to do much of this yourself.
Kinsta’s hack-free guarantee
The steps you need to take will depend on the way in which your site has been hacked, and you may not need to work through all of these. The steps we’ll go through are:
- Don’t panic
- Put your site in maintenance mode
- Reset passwords
- Use the Kinsta Malware Removal Service
- Update plugins and themes
- Remove users
- Remove unwanted files
- Clean out your sitemap
- Reinstall plugins and themes
- Reinstall WordPress core
- Clean out your database
Step 1: Don’t Panic
I know that the worst thing you can say to someone who’s panicking is “don’t panic”. But you need to have a clear head if you’re going to be able to diagnose and fix the problem.
If you can’t think straight, simply put your site in maintenance mode and leave it for a few hours until you’re feeling calmer. Which, again, sounds easier said than done yet it’s crucial here.
Step 2: Put Your Site in Maintenance Mode
You don’t want visitors finding your site in its compromised state and you also don’t want them seeing what your site will look like while you’re fixing it.
So put it into maintenance mode, if you can.
If you can’t log in to your WordPress site right now, this won’t be possible, but as soon as you can, come back and do this.
A plugin like Coming Soon Page & Maintenance Mode will let you put your site into maintenance mode, making it look as if it’s undergoing scheduled maintenance rather than being fixed after a hack.

Coming Soon Page & Maintenance Mode plugin
Once you’ve done that, you can relax a little knowing that people can’t see what’s going on.
You can configure the plugin to add a logo and customize the colors or you can just type in some quick explanatory text and leave it at that.
Now you can see your broken site but other people can’t.
Step 3: Use Kinsta Malware Removal Service
To save yourself the hassle of all the steps below, you can purchase the Kinsta malware removal service for a one-off fee of $100 when migrating to Kinsta. Important: if you are a Kinsta client, this is included in your plan!
If you don’t want to do this, or can’t afford to, read on to learn more on how to clean up your hacked site.
Step 4: Reset Passwords
Since you don’t know which password was used to gain access to your site, it’s important to change all of them to prevent the hacker from using them again. This isn’t confined to your WordPress password: reset your SFTP password, your database password, and your password with your hosting provider too.
You’ll need to ensure that other admin users reset their passwords too.
Step 5: Update Plugins and Themes
The next step is to make sure all of your plugins and themes are up to date. Go to Dashboard > Updates in your site and update everything that’s out of date.
Want to know how we increased our traffic over 1000%?
Join 20,000+ others who get our weekly newsletter with insider WordPress tips!
You should do this before attempting any other fixes because if a plugin or theme is making your site vulnerable, any more fixes you make could be undone by the vulnerability. So make sure everything’s up to date before you proceed.
Step 6: Remove Users
If any admin accounts have been added to your WordPress site that you don’t recognize, it’s time to remove them. Before you do this, check with any authorized administrators that they haven’t changed their account details and you just don’t recognize them.
Go to the Users screen in your WordPress admin and click the Administrator link above the list of users. If there are any users there who shouldn’t be, click the checkbox next to them, then select Delete in the Bulk Actions dropdown list.
Step 7: Remove Unwanted Files
To find out if there are any files in your WordPress installation that shouldn’t be, you’ll need to install a security plugin like WordFence, which will scan your site and tell you if there are any files there that shouldn’t be, or use a security service such as Sucuri.
If you’re on a Kinsta hosting plan, you don’t need to install additional security plugins. This will interfere with the configuration of your site and could impact on performance. Instead, raise a support ticket and support we will fix your site.
Step 8: Clean Out Your Sitemap and Resubmit to Google
One cause of a site being red-flagged by search engines can be your sitemap.xml file being hacked. In one case we fixed at Kinsta, a sitemap had been infected with spurious links and foreign characters.
You can regenerate your sitemap using your SEO plugin but you’ll also need to tell Google that the site has been cleaned. Add your site to Google Search Console and submit a sitemaps report with Google to tell them you need the site to be crawled. This doesn’t guarantee that your site will be crawled immediately and can take up to two weeks. There’s nothing you can do to speed this up so you’ll have to be patient.
Step 9: Reinstall Plugins and Themes
If your site still has problems, you’ll need to reinstall any plugins and themes that you haven’t already updated. Deactivate and delete them from your Themes (here’s how to safely delete a WordPress theme) and Plugins pages, and reinstall them. If you didn’t already put your site into maintenance mode, do that first!
If you bought a plugin or theme from a plugin or theme vendor and you aren’t sure how secure it is, now’s the time to consider whether you should continue using it. If you downloaded a free theme/plugin from anywhere other than the WordPress plugin or theme directories, don’t reinstall it. Instead, install it from the theme or plugin directory or buy the legitimate version. If you can’t afford it, replace it with a free theme/plugin from the theme or plugin directory that does the same or a similar job.
If this doesn’t fix the problem, check the support pages for all of your themes and plugins. It may be that other users are experiencing problems, in which case you should uninstall that theme or plugin until the vulnerability has been fixed.
Step 10: Reinstall WordPress Core
If all else fails, you’ll need to reinstall WordPress itself. If the files in the WordPress core have been compromised, you’ll need to replace them with a clean WordPress installation.
Upload a clean set of WordPress files to your site via SFTP, making sure you overwrite the old ones. It’s a good idea to take a backup of your wp-config.php and .htaccess files first, in case these are overwritten (although they shouldn’t be).
If you used an auto-installer to install WordPress, don’t use that again as it will overwrite your database and you’ll lose your content. Instead, use SFTP to upload the files only. If you’re on Kinsta and used our WordPress installer, you don’t need to worry about this step anyway as we’ll replace WordPress core for you as part of our hack fix service.
Step 11: Clean Out Your Database
your database has been hacked, you’ll need to clean that out too. It’s a good idea to clean out your database as a clean database will have less stale data and take up less space, making your site faster.
Concerned with low-quality, DIY security from your host? Kinsta is built with security and performance in mind and provides support from WordPress experts available 24/7/365. Check out our plans
How do you know if your database has been hacked? If you’re using a security plugin or service, running a scan via that will tell you if the database has been compromised (or you may have been sent an alert). Alternatively, you can use a plugin like NinjaScanner which will scan your database.
The WP-Optimize plugin will let you clean out your database and optimize it for the future.
How to Prevent Your WordPress Site from Being Hacked
So you’ve cleaned up your site and you’ve reset your passwords so it’s a bit more secure than it was before.
But there’s more you can do to prevent future hacks and avoid the same thing happening again.
1. Ensure All Passwords Are Secure
If you haven’t already, make sure that all passwords relating to your website, not just your WordPress admin password, are reset and that you’re using strong passwords.
A security plugin will let you force users to use secure passwords, or if you’re with Kinsta it comes built-in with your hosting plan.
You can also add two-factor authentication to your site to make it harder for hackers to create an account.
2. Keep Your Site Updated
It’s important to keep your site up to date. Every time your theme, plugins or WordPress itself are updated, you should run that update, as it will often include security patches.
You can enable automatic updates either by editing your wp-config.php file or by installing a plugin to do it for you. If you’d rather not do that because you want to test updates first, a security plugin will notify you when you need to run an update.
When you update your site, make sure you do it properly, creating a backup and testing updates on a staging server if you have one. Kinsta plans include automated backups and a staging environment for all sites.
3. Don’t Install Insecure Plugins or Themes
When installing WordPress plugins in future, make sure they’ve been tested with your version of WordPress and that you’re downloading them from a reputable source.
Always install free plugins and themes via the theme and plugin directories: don’t be tempted to get them from third-party sites. If you’re buying premium themes or plugins, check the reputation of the plugin vendor and ask for recommendations.
4. Clean Out Your WordPress Installation
If you’ve got any themes or plugins installed but not activated, delete them. If you have any files or old WordPress installations in your hosting environment that you aren’t using, it’s time to remove those. Delete any databases you aren’t using too.
If you’ve got old, unused WordPress installations on your server, they will be particularly vulnerable, as you’re unlikely to keep them up to date.
5. Install SSL on Your Site
SSL will add a layer of security to your site and is free. Kinsta plans include SSL for no extra cost. If your hosting provider doesn’t provide free SSL, you can use the SSL Zen plugin to add free Let’s Encrypt SSL.
6. Avoid Cheap Hosting
Cheap hosting means you’ll be sharing server space with hundreds of other clients. This will not only slow down your site, but it will also increase the chances of one of those other sites introducing insecurity to the server.
Cheap hosting providers are less likely to robustly monitor server security or to help you if your site is hacked. A quality hosting provider like Kinsta will give you a hack-free guarantee and work hard to keep your site secure.
7. Set up a Firewall
A security plugin or a service like Cloudflare or Sucuri will let you configure a firewall for your site. This will add an extra barrier for hackers and reduce the chances of hacks and DDoS attacks on your site.
Here at Kinsta, all of our customers’ WordPress sites are protected by Google’s enterprise-level firewall. We also provide users with an easy to use IP Deny tool in MyKinsta to block malicious IP addresses.
8. Install a Security Plugin
If you install a security plugin on your site, it will notify you of any suspicious activity. This might include unauthorized logins or the addition of files that shouldn’t be there.
Again, refer to the warning provided by the plugin to work out what the problem is.
Reminder: If your site is hosted with Kinsta, you don’t need to install security plugins. This is because Kinsta provides all the security features you need.
9. Consider A Security Service
If you aren’t a Kinsta user, you might want to consider a security service like Sucuri, which will monitor your site and fix it if you’re hacked again.
Sucuri
It’s not cheap, but if your website is essential to your business income, it can pay for itself. There are different plans that offer varying turnaround times for security fixes. Sucuri will monitor your site, alert you if there’s a security breach, and fix it for you. Meaning you don’t have to go through the process of cleaning your site yourself again.
Alternatively, Kinsta hosting plans come with security features including DDoS detection, uptime monitoring, hardware walls, and a hack-free guarantee, meaning that if your site is hacked, we will clean it up for you. If you switch to Kinsta, we’ll migrate your site for you for free and clean it up if it’s hacked in the future. Make sure to check our curated list of the best WordPress migration plugins.
Summary
Having your website hacked is an unpleasant experience. It means your site isn’t available for users, which could impact on your business. It will mean you have to take swift action, which will impact on your other activity.
Here’s a recap of the steps you need to take if your site is hacked:
- Reset passwords.
- Update plugins and themes.
- Remove users that shouldn’t be there.
- Remove unwanted files.
- Clean out your sitemap.
- Reinstall plugins and themes, and WordPress core.
- Clean out your database if necessary.
And remember: following the steps above to prevent hacks will avoid you having to do all this again in the future: it pays to keep your site as secure as possible.
If you enjoyed this article, then you’ll love Kinsta’s WordPress hosting platform. Turbocharge your website and get 24/7 support from our veteran WordPress team. Our Google Cloud powered infrastructure focuses on auto-scaling, performance, and security. Let us show you the Kinsta difference! Check out our plans





